Managed Detection
and Response
Unlike traditional security solutions that may only provide alerts, MDR services offer a comprehensive approach by combining technology with human expertise to proactively hunt, investigate, and mitigate threats.
ALL-IN-ONE MDR SERVICE
Don't Settle for Partial Security. Multi-Signal MDR Matters.
At Infinitio, we believe a multi-signal approach is paramount to protecting your complete attack surface.
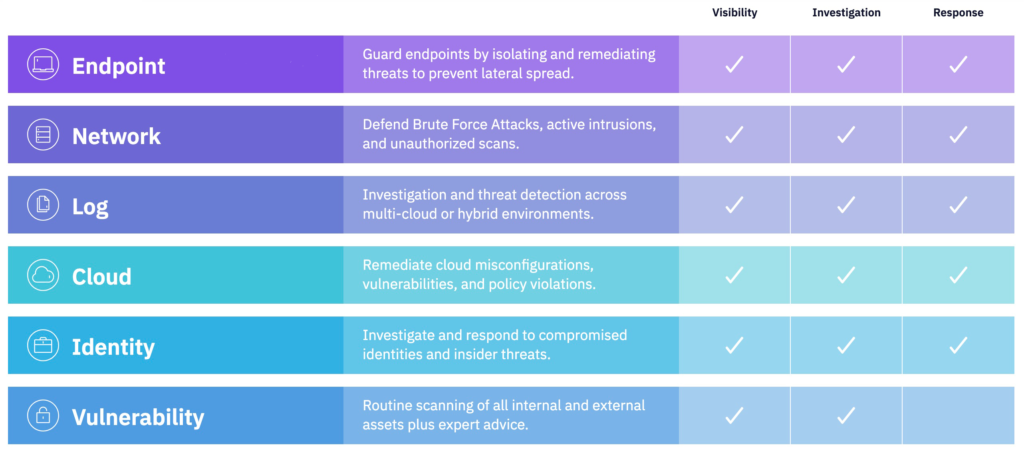
We partner with industry leading open XDR platforms. There is no one size fits all and we work with you to make sure we capture your unique requirements, team makeup, and more to provide the best solution. All of our platforms ingest high-fidelity data sources from endpoint, network, log, cloud, identity, assets, and vulnerability data to enable complete attack surface visibility. Our open XDR platform provides automated blocking capabilities to prevent attackers from gaining an initial foothold while our expert Threat Hunters initiate human-led threat investigation and containment at multiple levels of the attack surface.
Through host isolation, malicious network communication disruption, account-based suspensions, and other measures, we can stop the attacker at any level.
Our Powerhouse of Managed Cybersecurity
One platform. Your complete attack surface, protected.
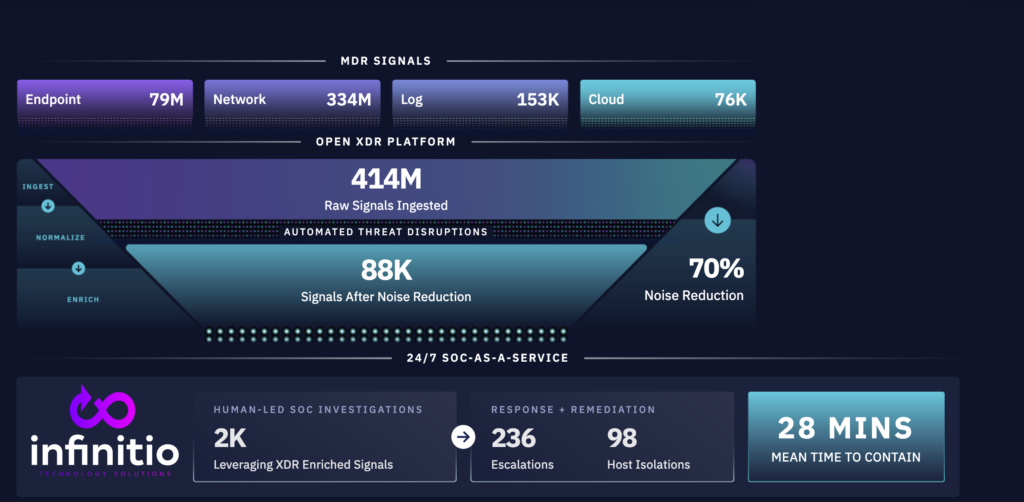
With a Mean Time to Contain of 15 minutes or less, our powerful open XDR Platform ingests network, cloud, log, endpoint, and identity signals, correlating indicators of compromise to detect, respond to, and automatically disrupt threats in minutes.
Seamless Integration and Threat Investigation Across Your Existing Tech Stack
Our MDR service integrates seamlessly with the existing tools and SaaS platforms in your environment to enable continuous monitoring across your hybrid footprint, ingestion of high-fidelity data sources, and 24/7 protection from sophisticated known and unknown cyber threats with proactive threat hunts. We continuously expand our multi-signal ingestion capabilities by adding new detections and runbooks for SaaS platforms and enterprise applications. When suspicious activity is detected, we stitch together context-free telemetry to identify similar attacker tactics in your environment.



